BURPSUITE:AUNTENTICACIÓN WEB ..Hackeando vamos ..
Hacking web authentication "Madrid".. Recordando "BurpSuite" ...
Hoy alguien, en una "conversación" me ha preguntado
Juan Carlos, que piensas de BurpSuite? .... Si os digo la verdad me hubieran faltado horas para explicar todo lo que conozco de BurpSuite, pero he preferido alabar su Proxy existente dentro de esta Suite de Test de Penetration en Aplicaciones Web .. o no web .. ahora me explico, porque también he estado observando por foros y otros artículos donde solo se nombra a BurpSuite como una Tools para Pentest ...
Bueno , en mi "humilde" opinión cuando se creó el "Spider" de BurpSuite precisamente no estaban pensando en hacer pentest a empresas, no majetes no .. lo que ocurrió con BurpSuite es como todo .. que los hackers tenemos que comer .. y crearon una herramienta "acojonate" donde los MiTm son cosas de "risa" .. aunque la verdad para hacer un Man In The Middle no es que haya que ser un "Gurú" .. pero si que es verdad que podeís estar pensando
RECORDANDO MAN IN THE MIDDLE .. Un poquito anda ...
"Si todos decís lo mismo pero nadie explica paso a paso como hacer un "ManInTheMiddle" ... sois todos iguales, esto es una película .. y además, eso es un lío .. no se qué de envenenar .. o era suplantar ... bueno no se, algo así ... la ARP y hacer pensar al otro tío que tu eres el "bueno" y así te quedas con todo lo que pase por en medio ... eso es una película, y además, no entiendo ni "papa" ... hablaís raro y sois raros ... "
Para los que esteís pensando esto o cosas similares o simplemente quereís hacer ya de una vez un Man In the Middle .. pues mirar, directamente hay que ser muy muy lelo para no encontrar manuales a día de ayer de como hacer un MiTM, paso a paso y desde cero ..
Por cierto, existe suplantacíón y envenenamiento .. por lo tanto, los ManInTheMiddle son muy extensos .. pero no en la técnica, sino en los escenarios sobre los que es posible hacer un MItM
Pero os voy a dejar unos videos anda ...
Un Poquito de Chicha
Cain Y Abel .. me encanta !!!
Ahora en Wireless
Pero como he oído paso a paso .. pues esa es la pista que teneís ... si vaís camino de ser hacker, con "paso a paso" y google teneís lo que vosotros quereís ... porque no es el motivo de este Post explicar ( otro día quizás ..) como hacer un MitM ... Sinceramente me aburriría menos explicándo un Man In The Browser ... por ejemplo !!! ainsssssssss
BURPSUITE .. ENTRANDO EN MATERIA S3RI4 ...
Mascadita la técnica .. que conste en acta señoría !! :P
Ah majetes en Inglés, porque desde Facebook me están diciendo .. y lo entiendo ( Siria, Pakistan y Usa que tiré de su idioma y como Burp mejor bajarlo en Inglés ... )
Pasitos ( For Dummies ..) :P
1. Set the browser proxy to Burpsuite
2. In the Burpsuite, go to Proxy -> Intercept -> "Intercept is on"
3. Go to Proxy -> Option -> "generate CA-signed per-host certificates" for each time the
user connects to a SSL protected website, Burpsuite will generate a server certificate for
that host, signed by a unique CA certificate which is generated in Burpsuite during its
installation. The purpose of this is to reduce the SSL errors that occur because of the
proxy in between
1)HTTP-Basic Authentication
HTTP-Basic authentication uses a combination of a username and password to authenticate
the user. The process starts when a user sends a GET request for a resource without providing
any authentication credentials. The request is intercepted by Burpsuite and looks something
like this.
The server responds back with a “Authorization Required” message in its header. We can
see the packet in Wireshark. As we can see from the header, the authentication is of the
type “Basic”. The browser is quick to recognize this and displays a popup to the user
requesting for a Username and a Password. Note that the popup is displayed by the
browser and not the web application.
Once we type in the username and password and intercept the request again using
Burpsuite, we get something as shown in the figure below.The last line says
“Authorization: Basic aW5mb3NlYzppbmZvc2VjaW5zdGl0dXRl”. This is basically the extra
thing being passed in the header now. The text after Basic holds the key. These are
basically the credentials in encoded form.The username and password are concatenated
with a colon (:) in between and the whole thing is then encoded using the Base64
algorithm
One of the problems with HTTP-Basic Authentication is that the data is being passed over
in plaintext. This risk can be removed by using SSL, which will send the data in encrypted
format, and hence the value in the Authorization header will not be visible. However it
will still be vulnerable to many client side attacks, including MITM. It is also vulnerable to
Brute force attacks which we will see in the coming sections
2)HTTP-Digest Authentication:
Digest Authentication was designed as an improvement
over the HTTP Basic Authentication. One of the major improvements is that the data is
not passed over in cleartext but in encrypted format. The user first makes a request to the
page without any ... any what ... any credentials. The server replies back with a WWW-
Authenticate header indicating that credentials are required to access the resource. The
server also sends back a random value which is usually called a “nonce”. The browser then
uses a cryptographic function to create a message digest of the username, password,
nonce, the HTTP methods, and the URL of the page. The cryptographic function used in
this case is a one way function, meaning that the message digest can be created in one
direction but cannot be reversed back to reveal the values that created it.
By default,Digest authentication uses MD5cryptographic hashing algorithm.
bUT ... HAHAHA!!! ....Digest Access authentication is less vulnerable to Eavesdropping attacks than Basic
Authentication, but is still vulnerable to replay attacks, i.e., if a client can replay the
message digest created by the encryption, the server will allow access to the client.
However, to thwart this kind of attack, server nonce sometimes also contains timestamps.
Once the server gets back the nonce, it checks its attributes and if the time duration is
exceeded, it may reject the request from the client. One of the other good things about
Digest access authentication is that the attacker will have to know all the other 4 values
(username, nonce, url, http method) in order to carry out a Dictionary or a Brute force ....attack of course lusers ....
This process is more computationally expensive than simple brute force attacks and also
has a larger keyspace which makes brute force attack less likely to succeed.
3)Form Based Authentication: Form Based Authentication uses a form (usually in html) with input tags to allow users to enter their username and password. Once
the user submits the information, it is passed over through either GET or POST methods
via HTTP or HTTPs to the server. On the server side if the credentials are found to be
correct, then the user is authenticated and some random token value or session id is given
to the user for subsequent requests. One of the good features of Form Based
authentication is that their is no standardized way of encoding or encrypting the
username/password, and hence it is highly customizable, which makes it immune to the
common attacks which were successful against HTML Basic and Digest Authentication
mechanisms. Form Based Authentication is by far the most popular authentication method
used in Web applications. Some of the issues with Form Based Authentication is that
credentials are passed over in plaintext unless steps such as employment of TLS (Transport
Layer Security) are not taken.
BurpSuite...Attacking Web Authentication
1. Go to the form and submit a request using anyusername/password for now, then intercept the request
........ Once you have the request, right click on it and click on “send to intruder”
2. Go to intruder tab -> under the target tab -> configure the target
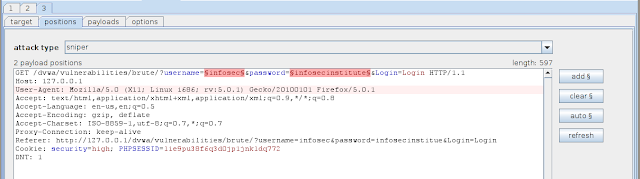
3. Go to position tab of intruder tab -> Hit clear button -> Highlighted user,password text and......................................................................................>
hit add button lusers ... ainssss !! :P
then the step 4..... Change the attack type "sniper" to "cluster bomb"
**Basically the idea of cluster bomb is to use Multiple payload sets (1 for username and 1 for the password). The attack will start by trying all the values in Payload 1 with first value in Payload 2, then by trying all the values in Payload 1 with second value in Payload 2 and so on. As we can see in the image below, our attack type is set to “Cluster Bomb”.
5. Go to payload tab -> select payload set 1
-> hit load button and
-> choose the file that contain list of username
6. select payload set 2 -> hit load button -> choose the file that contain list of password
easy .. and the step .....7. Go to option tab -> Selected “store requests” and “store response”
Come Hacker step 8. Click on intruder on the top left and click on “start attack”
Easy ... !!! i don´t know ....
If you want the detail of each step, please go to the Source. This post is just summarie
from the Source.
Source: http://resources.infosecinstitute.com/authentication-hacking-pt1/ç
Pues eso si quieres complentar esto pinchas arriba y tienes todo ... pero vamos que tienes en Google miles de fuentes a las que acudir mejores que yo ... o no, no lo se ..
Yo por lo menos hablo en dos idiomas jajajaja !!! :p